Key Features
Supporting Investigations as they emerge
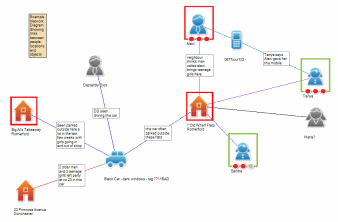
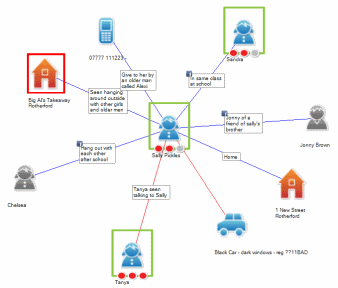
Dynamic interactive functions allow you to map and support investigations as they unfold in real time. Simple to use, associations can be created between victims, offenders, addresses, vehicles, telephone numbers and social media. Relationships, premises and individuals can be risk assessed in relation to particular inquiries as they unfold and the network is built on a white screen which can be projected to use during meetings. Screen grabs can be taken at each critical stage of the investigation to provide a historical record of how the investigation unfolded.
Mapping Complex Networks and utilizing your knowledge
Once your information and intelligence is loaded into the system you can create complex network maps to allow you to support big investigations and further interrogate the system to find new connections. The multi screen function allows you to highlight particular parts of a network or focus on one address or a group of victims. The search functions allow you to see all the associations with a particular, victim, offender, premises, vehicle or phone number.
Integrated Case Management to Support Victims
EDIS also supports the integration and coordination of a range of multi-agency support services to victims to ensure stability in their home placements, recovery and support to be resilient witnesses in the prosecution of offenders. The database can also be used to provide important anonymised performance outcome information for funders and other stakeholders.
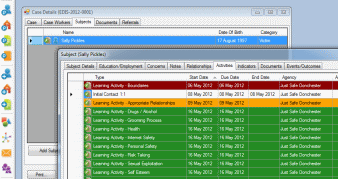
Detailed records of events/outcomes and case worker activities may be maintained and sets of indicators defined to risk assess individuals and monitor changes to key areas of vulnerability. Documents (including images, audio and video clips) relating to cases or individuals may be stored in the database
Security
EDIS operates around a secure Microsoft SQL Server database. EDIS runs as a Windows application and requires a secure network connection between client PCs and the database server. No data are cached on user's PCs or laptops.
EDIS supports a range of user roles which grant or restrict access to various parts of the system. These include case manager and case worker roles, agency administrator, superuser and a read-only guest role. Only suitably authorised users have access to sensitive case information. Audit records are maintained for key events such as login attempts, searches and access to documents, case and individual's records.
Documents are stored within the database and cannot be accessed outside EDIS. Document sharing between agencies is possible and is under full control of the agency which owns (uploads) the document.
EDIS mail provides a means of secure messaging between case workers across and within agencies. All messages and attachments are stored within the EDIS database.